On August 13 2025, Iru's security researchers discovered a potentially interesting Rust-compiled file on VirusTotal. Our investigation resulted in the analysis of 6 related Mach-O files. With this initial blog post, we're focusing on the first file of this analysis, the dropper. The dropper file is designed to quietly download and run another malicious file, stay on the system by setting up persistence, and avoid being detected by commonly used macOS security tools.
We have included the hashes of the relevant Mach-O files currently on VirusTotal in the IOC section below in an effort to shed light on these samples quickly while we continue our analysis of the loader samples. At the time of writing, the specific Mach-O we cover below has zero detections on VirusTotal and most of the loader Mach-O files are also undetected.

Artifacts of Interest
Dropper
dropper-6e82280a9b4b5544 - (nvh82ks.pyd)e98756472404aeef70ba4d403339962989d9ed733fa0f6a23bdf4c2900d7e877
Download Domain (No longer active upon discovery)
hxxps://p92nd.pages.dev/lsjnc8t.avif2
Technical Analysis
Dropper

This first sample that we will cover is an adhoc signed binary that is written in Rust. Interestingly, the Identifier of this Mach-O contains the name dropper, which served as a hint for our analysis. Given that we are analyzing a Rust Mach-O executable, we need to take into account that Rust strings are not null terminated so it is important to properly parse them and understand where they are referenced in the code.
With quick analysis of the sample’s strings, we were able to focus on specific strings that provided details of its behavior. Certain strings immediately stood out including the names of known macOS security tools written by Patrick Wardle, which we explore next.
![]()
Objective-See Tool Queries
Looking for the cross references of the KnockKnockBlockBlock characters seen in the screenshot above led us to the sub_1000029f0 function. Here, we can see LuLu, KnockKnock, and BlockBlock strings being initialized along with pgrep, which would indicate the usage of the pgrep command utility.

The pgrep commandline tool will return the Process Identifiers (PIDs) of these tools if they are running. These PIDs appear to then be passed to a kill command if running. This indicates an attempt by the malware to be aware of commonly used macOS security tools. In the initial screenshot showing Patrick’s tools, we can see a reference to a property list (.plist) file in the /Library/LaunchAgents directory, so we will continue our analysis of this function looking for the persistence setup.
Plist Persistence Setup
Below, we can see a large string for the contents of a plist that is used for setting persistence on the infected machine.

We do not see the Label NAME variable or the ProgramAguments PROGRAM variable in this string, so we will need to find where this plist is referenced in the code to gain insight into this persistence.

Using the cross references to this string, we can replace these variables, which will help with the identification of this sample.
Label = com.apple.updeventsd
ProgramArguments = /Users/Shared/.updeventsd
launchctl to load this plist and set the persistence. The path to the plist results in:~/Library/LaunchAgents/com.apple.updevents.plist
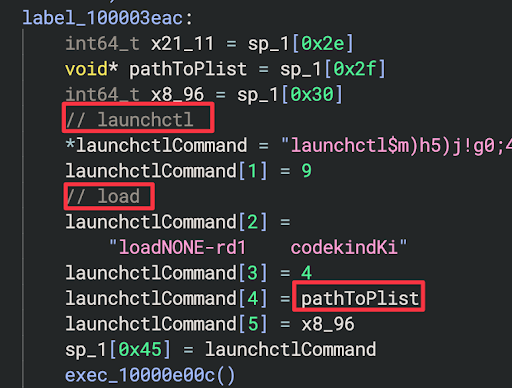
The /Users/Shared/.updeventsd path corresponds to the name of the next stage that is downloaded via curl, which is executed prior to the execution of the launchctl call. Next, we will cover the curl execution and next stage setup.
Curl and Next Stage Setup
To understand how the next stage is dropped, we can look for the setup and execution of curl. In this same function, we can see the curl command string being set up which includes the Command and Control (C2) server:
hxxps://p92nd.pages.dev/lsjnc8t.avif2

The curl output is written to /Users/Shared/.updeventsd as a hidden file, which will be executed next after it is prepared.
updeventsd Setup
After the curl command is completed successfully, the downloaded Mach-O named updeventsd, which we will cover in the next blog post, is set up for execution. We can see this setup below by parsing the addresses of the strings related to the command which references the file path of the hidden next stage binary.

Commonly used commands including xattr -c and chmod 777 are executed to clear extended attributes and apply the appropriate permission bits for the next stage to be executed. The parsing of sh and -c strings passed along with their size of 2 bytes for the shell execution can also be seen in the screenshot above.
To remain hidden after downloading the next stage and installing the persistent item, this malware sample leverages a known technique to avoid prompting the user. Let’s cover that next.
Notification Silencing
This sample does install persistence, but in order to attempt to remain hidden it uses a known technique to silence notifications from prompting the user of the newly installed LaunchAgent. It does this by obtaining the PIDs for NotificationCenter and usernotificationsd and executing the kill command line utility with the -STOP argument. We can see the command setup in the screenshot below.

This will attempt to suspend these two binaries which are used for notification prompts and aid in silently installing the persistence of the next stage.
What’s Next: Next Stage Analysis
This post represents the first stage of our analysis of the RustyPages malware, focused on the dropper component. To ensure rapid awareness and industry response, we’ve prioritized sharing key findings and IOCs while we continue our investigation of the loader samples.
We have updated Iru's detection logic to identify and protect our customers from this sophisticated threat. Our team is actively analyzing the next stage, which includes behaviors such as:
- Interaction with the Solana blockchain
- Pasteboard access and parsing
- Application window targeting techniques
IOCs
Mach-O Binaries
e98756472404aeef70ba4d403339962989d9ed733fa0f6a23bdf4c2900d7e877 - dropper
7ab47b7b14f4d6848b9f4d410d1315ccc68e9a6714d94a2e870b6ba77d28e828 - dropper
5cee6368c6a9922a81a03831979947db8e5365986b4ad725c552ab6018a083b3 - 1.0.5
204bae0402d68b89e729144fd92950f8c832d029320b50b030eacb81c0b8b3ea - 1.0.4
d2c48f4fa4b0285889ef6c7667e12a1c0eda1393632ef2eac67b32777bf096f7 - 1.0.4
f4c41111960771e0d7558ec2453b76ba9c422fcb9408e09a8de1fd611c272846 - 1.0.2
Network
hxxps://p92nd.pages.dev
hxxp://103.245.231.111:44974/
hxxp://93.115.172.151:45259/
